Are your services secure?
In today’s world, you can hardly go a week without reading in the news about security breaches, malware, and more. We’ve already had headline news this year for Wanna Cry{:target="_blank"}, and now there are dozens of copycat malware programs taking advantage of out-of-date systems. Think of all the services that your company uses from error monitoring to logging and APM. Some of them may be delivered by vendors and others set up by internal teams. Did your IT team evaluate these services to determine how secure they are? If not, you might want to reconsider the services you use or who can best deliver them.
Unfortunately, many companies only do the bare minimum due to time constraints, limited budget, lack of expertise, etc. Real security is hard because threats are constantly evolving, and they target the weakest link across all layers of your organization. Companies make good targets because they concentrate data from potentially billions of customers in one place. Their infrastructure can have millions of lines of code that no one person fully understands. They often rely on a complex and poorly monitored network of third-party service providers, offshore contractors, platforms, modules, etc. These all present opportunities to attack.
Sophisticated companies evaluate the security of their service providers when making a purchase, and they hold internal services to the same standards. They typically have a checklist of security requirements covering certifications, security audits, data management processes, etc. Companies in the EU or US-regulated industries like finance and healthcare may have additional legal requirements like PCI-DSS and HIPAA. They require their service providers to be complaint, particularly when sensitive customer data is being handled. Even if your company is not regulated in this way, these certifications can signal that a company takes security seriously.
Rollbar's advanced encryption at rest
Rollbar provides strong security to all our accounts through encrypted data transmission, secure authentication, regular penetration testing, and more. Additionally, we deliver a higher level of security to customers to who sign up for our Compliant SaaS solution. This solution complies with security and privacy standards like ISO 27001{:target="_blank"}, CSA STAR{:target="_blank"}, US-EU Privacy Shield{:target="_blank"}, and HIPAA for healthcare data. Our data center meets the stringent SOC 2 Type 2{:target="_blank"} standard, among others. We also implement a number of procedures for risk management and communication with our customers. Compliance is important because you don’t need to take our word for it, we have passed rigorous audits to prove it.
One key feature that lets us deliver better security is our encryption at rest. This means the data is encrypted when it’s stored inside our data center. Many other services do not offer encryption at rest, and store customer data in plaintext. This allows hackers to download the data if they are able to get access to one of the servers. This is how hackers were able to access millions of customers’ data in the Sony{:target="_blank"} data breach.
Some companies often confuse encryption at rest with disk-based encryption. This encrypts the hard disk so that if someone were to physically steal the hard disk they would not be able to access the contents. However, most attacks target computers while they are running and the disks are unlocked. That means malicious code or hackers could gain privileges using a vulnerable service on the computer and then read files in plaintext while the computer is running. Also, a breach could compromise all customers whose data on is on the disk.
Rollbar goes above and beyond to offer a more advanced form of encryption at rest. We encrypt in the application layer and use unique keys for each customer project. This prevents attackers from reading files in plaintext while the computer is running. It also separates customers and projects to limit the scope of an attack. We encrypt using the AES-256 GCM algorithm, the same one used by Amazon Web Services (AWS). Furthermore, we encrypt our customers’ historical data, in addition to data that’s newly coming in.
See it in action
You can see the status of encryption at rest under Account Settings –> Encryption. You can see when the encryption was activated and when the historical data encryption is complete.
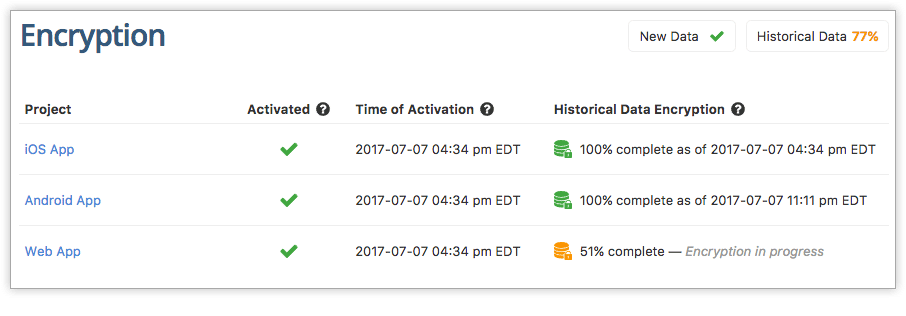
{: .imgcaption}
Encryption at rest as seen in Rollbar
Encryption at rest is currently available to customers of our Compliant SaaS solution. For more information, contact us to talk to a sales representative.
If you haven’t already, sign up for a 14-day free trial of Rollbar and let us help you take control of your application errors.


